Cortex XDR is the better choice to stop modern threats
SentinelOne’s fragmented XDR feature set is incomplete, with no user behavior analytics, network threat analytics, forensics or ability to group alerts into incidents. SOC analysts are forced to sift through a large number of alerts to see the complete picture that Cortex XDR provides automatically. Even worse, analysts must utilize multiple consoles, making management complex and reducing SOC efficiency. Their limited native data set, restrictive capabilities and over-reliance on third-party integration questions their claim as a legitimate XDR provider.
Cortex XDR goes far beyond SentinelOne’s EDR focus, delivering ML-powered behavioral analytics across multiple data sources, a simplified SOC workflow, incident management and much more – from one unified, cloud-based console. Learn why leading organizations trust Cortex XDR over SentinelOne to prevent, detect and respond to all threats.

Real XDR
SentinelOne is not a complete XDR solution. Over-reliance on their endpoint agent and its data, with no forensic capability or insight into unprotected endpoints, leaves security teams blind to the bigger picture. Cortex XDR® is the industry’s first true extended detection and response (XDR) platform, trusted by over 3,000 customers.
-
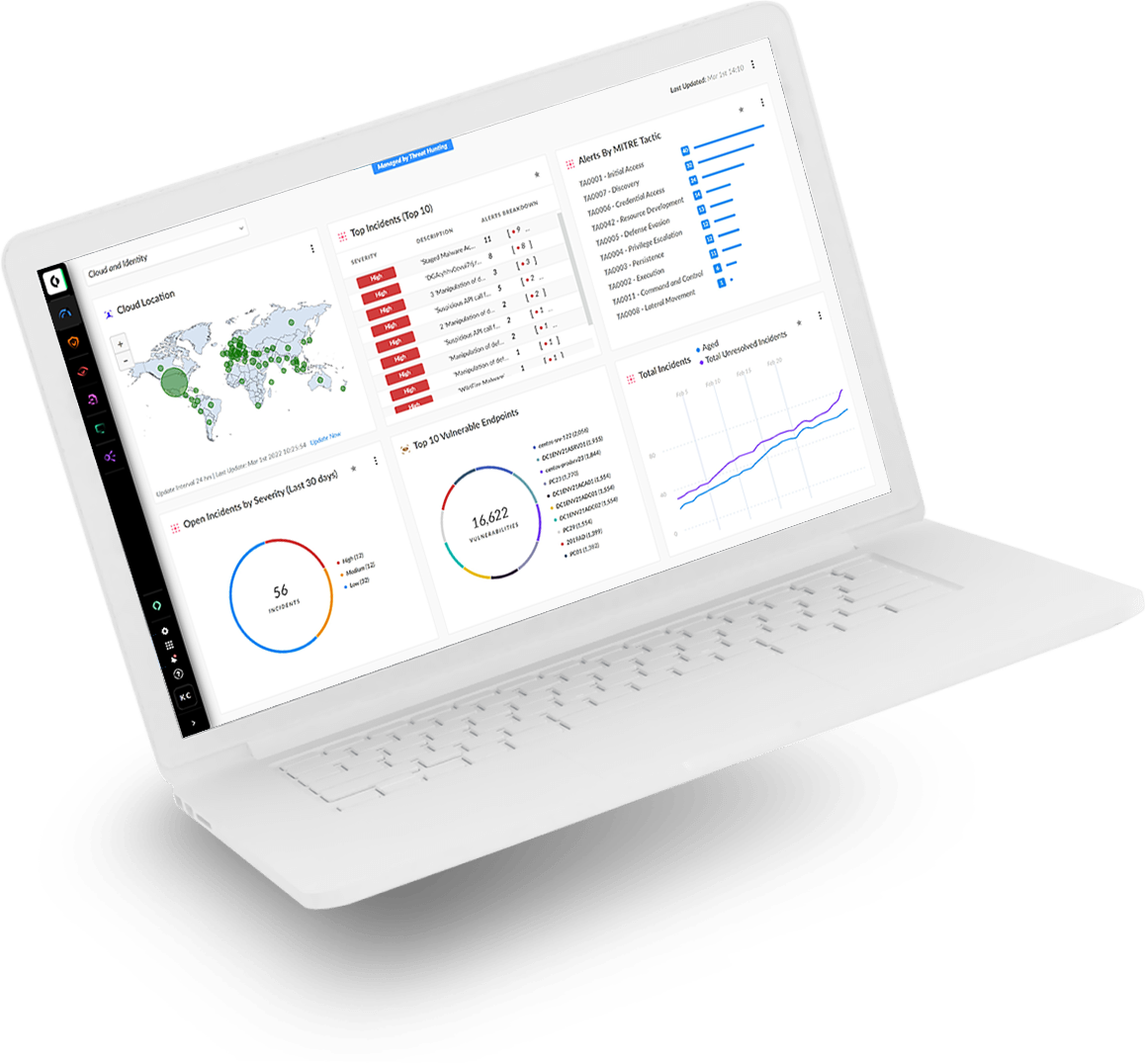
Cortex XDR advances security beyond just endpoint protection and data collection, integrating native network, cloud, identity and third-party data to stop modern cyberattacks.
-
Data from any source is automatically stitched together to reveal the root cause and timeline of alerts to identify and quickly put a stop to threats.
SentinelOne lacks several key capabilities, like user behavior analytics and forensic analysis, that help pinpoint anomalous behavior and enable quick investigation of alerts. And without integrated cloud sandboxing and real-time file analysis, SentinelOne’s customers may be exposed to new forms of malware. Cortex XDR’s robust features provide broader threat detection and investigation intelligence to enable fast incident response. Integration with our WildFire® malware prevention service goes beyond traditional sandboxing to detect unknown threats in a complete cloud analysis environment. Behavioral analytics analyzes data by tracking more than 1,000 behavior attributes to profile behavior and detect malicious activity. Host Insights combines vulnerability assessment, application and system visibility, along with a powerful Search and Destroy feature to help identify and contain threats across all endpoints.
Critical Feature Set

Simplified Workflow with Built-in Incident Management
A lack of incident management leaves SOC analysts who use SentinelOne overwhelmed by a barrage of individual alerts. Cortex XDR’s best-of-breed incident management helps to group, manage and resolve related alerts as incidents, reducing the number of individual alerts to review by 98%.*
-
With a single click, analysts can instantly reveal the root cause, reputation and sequence of events, lowering the experience needed to verify threats.
-
Customizable correlation rules allow analysts to define rules based on dozens of different parameters to help identify misuse of systems and applications and thwart evasion techniques.