Consolidated supply chain coverage and visualization
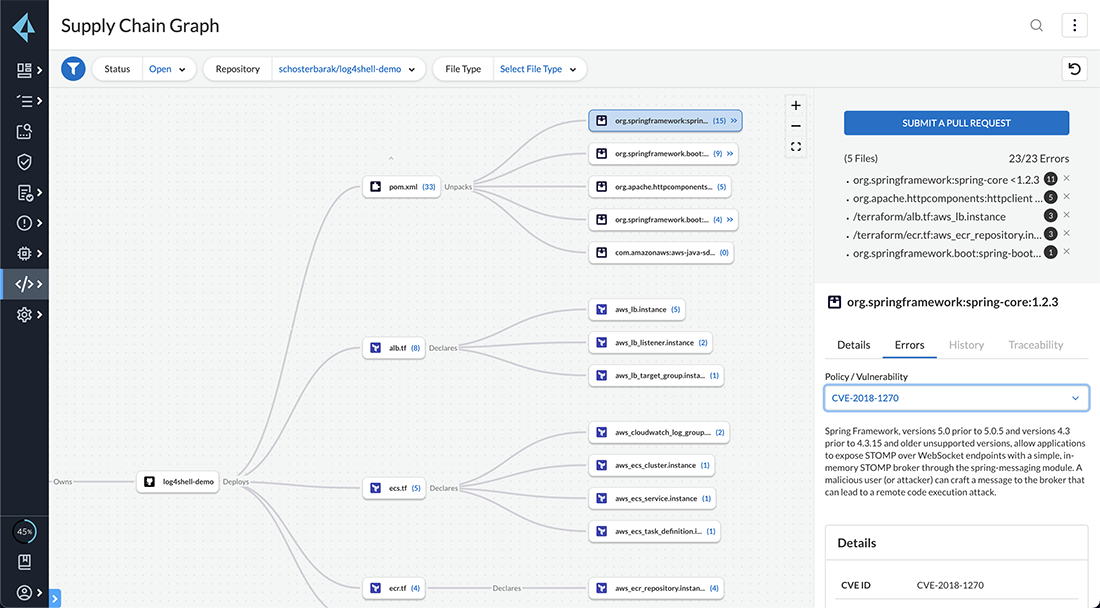
With Prisma Cloud’s Supply Chain Graph, organizations can visualize each component of their supply chain and understand all associated risks. Prisma Cloud’s Supply Chain Graph inventories all of an organization’s code and pipeline components into one visualization – augmented by an overlay of security posture data – to give a complete visual representation of an organization’s application and infrastructure asset dependencies. Using those insights, organizations can prioritize risks across their supply chain and more efficiently deploy resources to remediate the issues with the highest chance of exploitation.
-
Software supply chain visibility and cataloging
The Supply Chain Graph provides a consolidated inventory of organizations’ delivery pipelines and code components. By visualizing all of the connections, organizations gain much-needed visibility into their supply chain’s attack surface. Organizations can then take action based on those findings, like by leveraging Prisma Cloud’s bulk pull request fixes feature. This feature enables organizations to create a single pull request that will apply an automated fix for many violations at once.
-
Context-aware Software Composition Analysis (SCA)
Prisma Cloud supports open source package scanning with limitless dependency tree scanning and granular version bump fixes. By overlaying vulnerability findings with infrastructure misconfigurations and by embedding into developer tools, Prisma Cloud’s SCA empowers developers to prioritize and remediate open source risks faster.
-
Industry-leading IaC security
Powered by the market’s most robust open source policy-as-code engine, Checkov, Prisma Cloud is equipped with thousands of policies to help proactively enforce cloud security best practices. Prisma Cloud surfaces cloud security issues early in the development lifecycle and provides code fixes to ensure only secure infrastructure code gets deployed.