Backed by the community
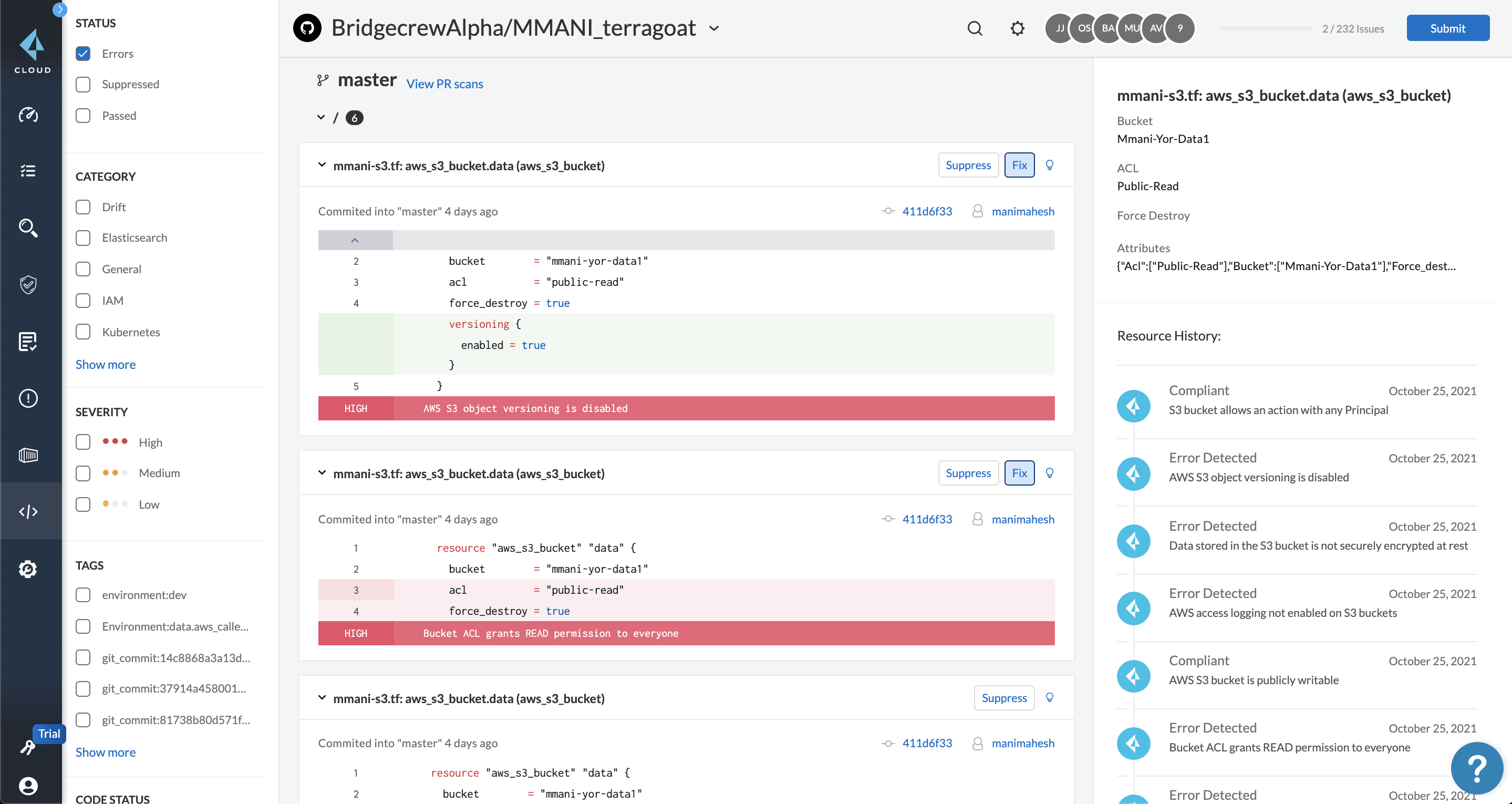
Prisma Cloud IaC security is built on the open source project Checkov. Checkov is a policy-as-code tool with millions of downloads that checks for misconfigurations in IaC templates such as Terraform, CloudFormation, Kubernetes, Helm, ARM Templates and Serverless framework. Users can leverage hundreds of out-of-the-box policies and add custom rules. Prisma Cloud augments Checkov with simplified user experience and enterprise features.
-
Check for policy misconfigurations
Checkov checks IaC templates against hundreds of out of the box policies based on benchmarks, such as CIS, HIPAA, PCI, and community sourced checks.
-
Leverage context aware policies
Checkov’s policies include graph-based checks that allow multiple levels of resource relationships for complex policies such as higher severity levels for internet facing resources.
-
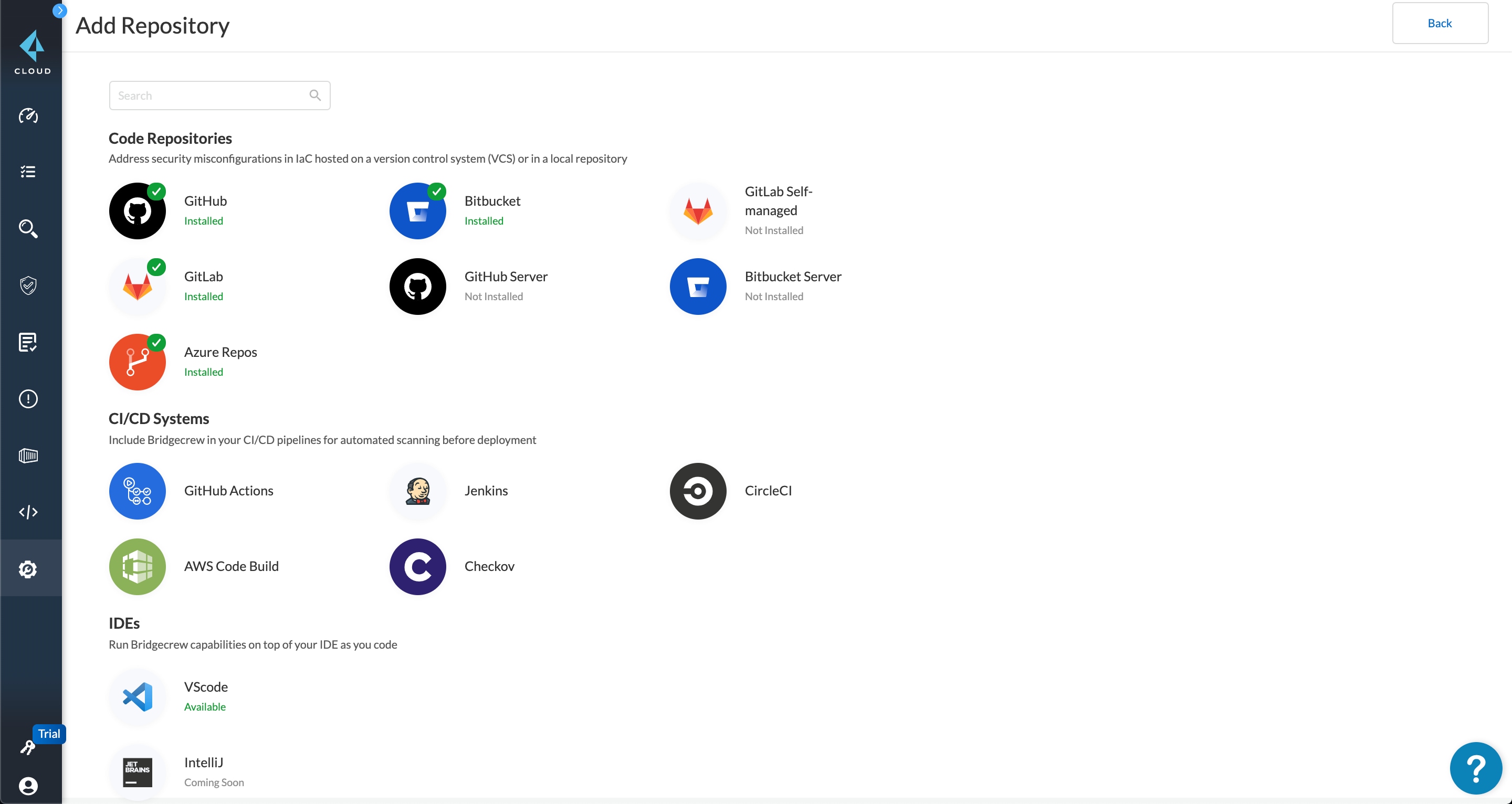
Extend capabilities and integrations
Checkov is designed to be extensible, with the ability to add custom policies and tags, as well as CLIs designed to be added to continuous integration and other DevOps tools.
-
Integrate with Prisma Cloud to extend its capabilities
Prisma Cloud augments Checkov’s open source capabilities with a history of scans, additional integrations, auto-fixes, Smart Fixes and more